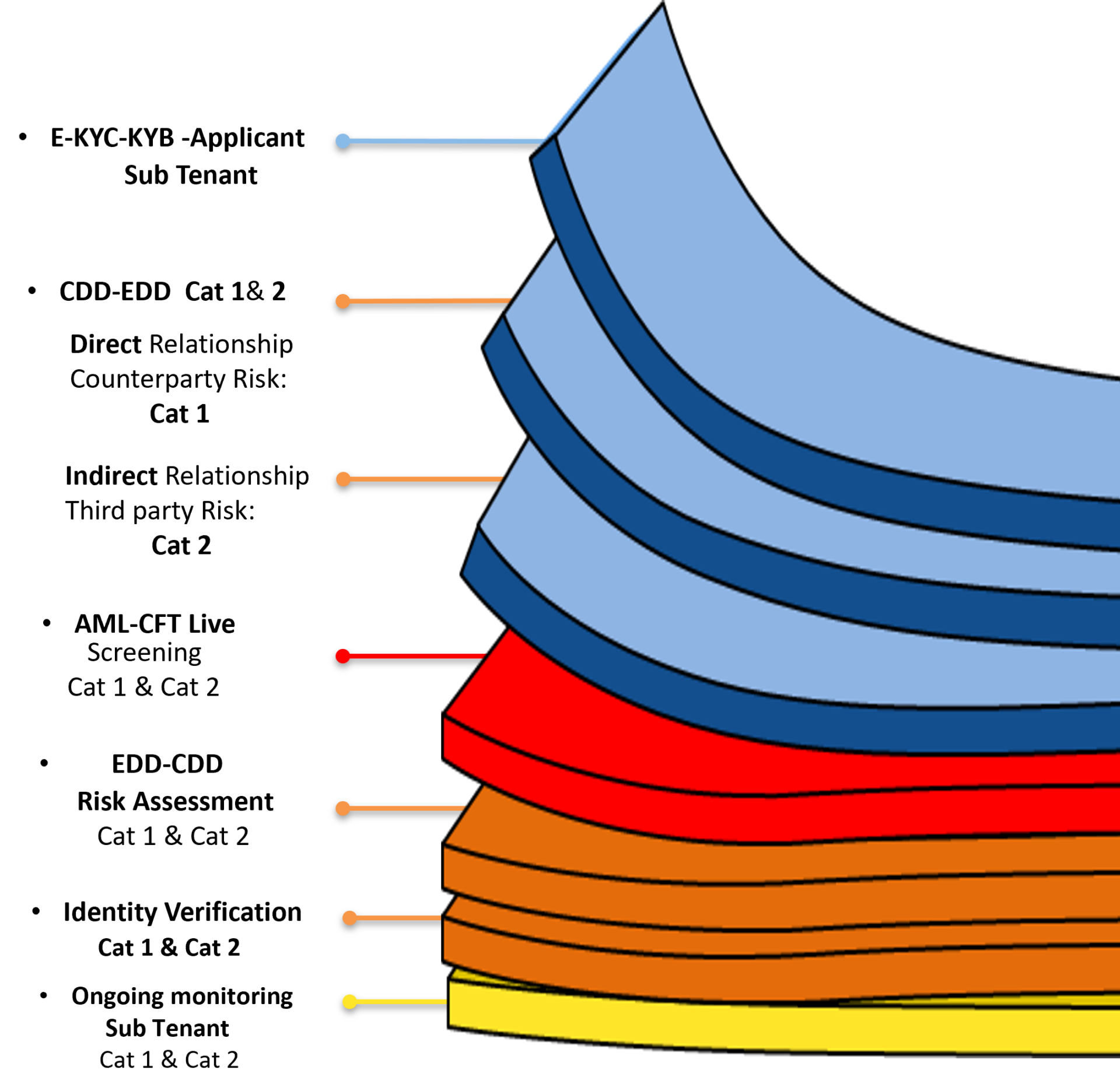
Level 3 Relevance Service: This process ensures compliance with international and local regulatory requirements, including FAFT international standards, country risk assessments, HKMA directives, and JFIU guidelines.
A thorough compliance framework that combines automated efficiency (Level 1) with human expertise (Level 2) and focused training to proactively mitigate risk.
Our framework ensures scalable monitoring (Level 1), informed decision-making (Level 2), and proficient readiness while also ensuring compliance, preventing financial crime, and upholding integrity across all relationships.
Level 3 Relevance: focuses on monitoring counterparties that have a direct business relationship as sub-tenants.
Level 3 Relevance: focuses on monitoring third-party sub-tenants that do not have a direct business relationship but are indirectly associated.
Both direct and indirect relationships require structured AML-CFT monitoring to mitigate financial crime risks.
The integration of Level 1 automated systems and Level 2 investigative risk assessments ensures regulatory compliance, enhances proactive threat detection, and optimises record retention practices in line with international and jurisdictional requirements.