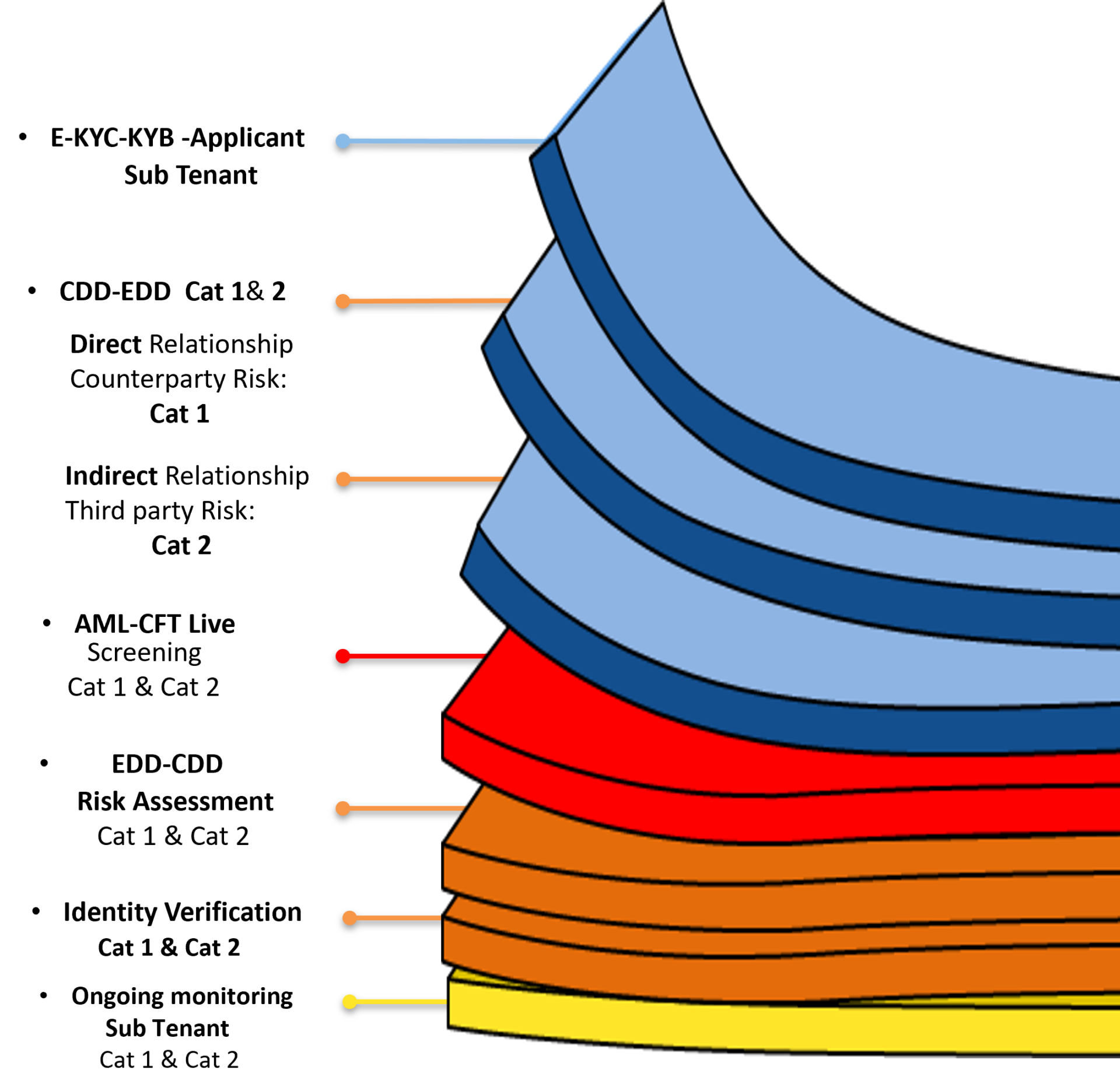
Level 2 Prospective services: Enhance due diligence (EDD) reviews the integrated Level 1 automated screening with manual verification and risk-driven analytics, ensuring thorough validation of counterparties, third parties, and their associated ownership structures.
This process mitigates money laundering and terrorist financing (ML/TF) risks, reduces and prevents financial crime, and addresses cross-border risks related to organised crime before approving tenants, sub-tenants, or customers for onboarding.
After validation, assign a risk rating (e.g., low/medium/high) to approved counterparties based on jurisdiction, ownership complexity, and ML/TF exposure.
Trigger STRs for: Mismatched source-of-funds documentation or modified documents post-approval. (where applicable).
Objective: Implement measures to verify the integrity of third-party partnerships and their transactional data, safeguarding against exploitation for illicit purposes.
Assign a risk rating to third parties after assessment, reflecting factors such as geographic risk, fund-source opacity, and crime links.
Trigger STRs for: Mismatched source-of-funds documentation or modified documents post-approval. (where applicable).
The framework adheres to global regulations by ensuring transparency of ownership (FATF), compliance with crypto regulations (EU), third-party checks (Hong Kong), and enforcement of sanctions (U.S.). It prevents financial crime by stopping fraudulent trade activities, illegal crypto schemes, and abuse of fake companies.
This collaboration resource shields each Tenant’s business, its Sub-Tenants, Partners, and activities, and blocks cross-border illicit networks, ensuring compliance within its ecosystem.
Note: Level 3 Relevance: (ongoing monitoring) is excluded here but ensures post-approval compliance.